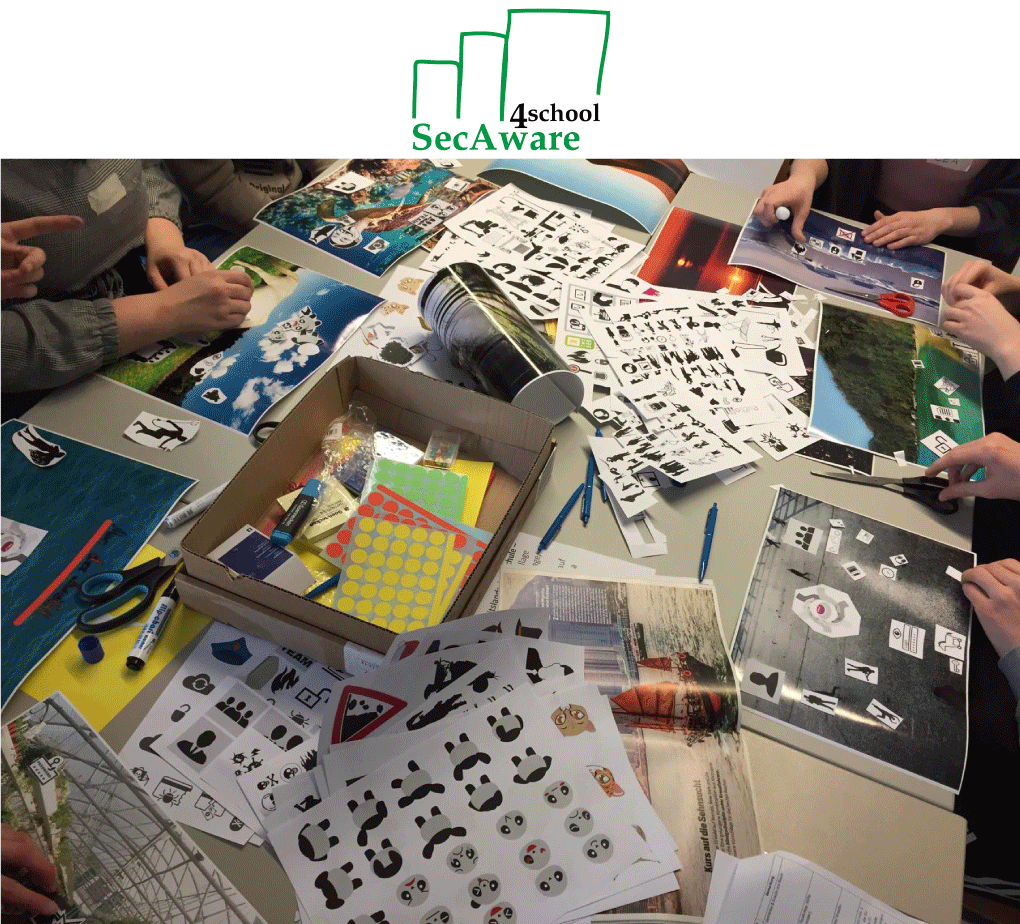
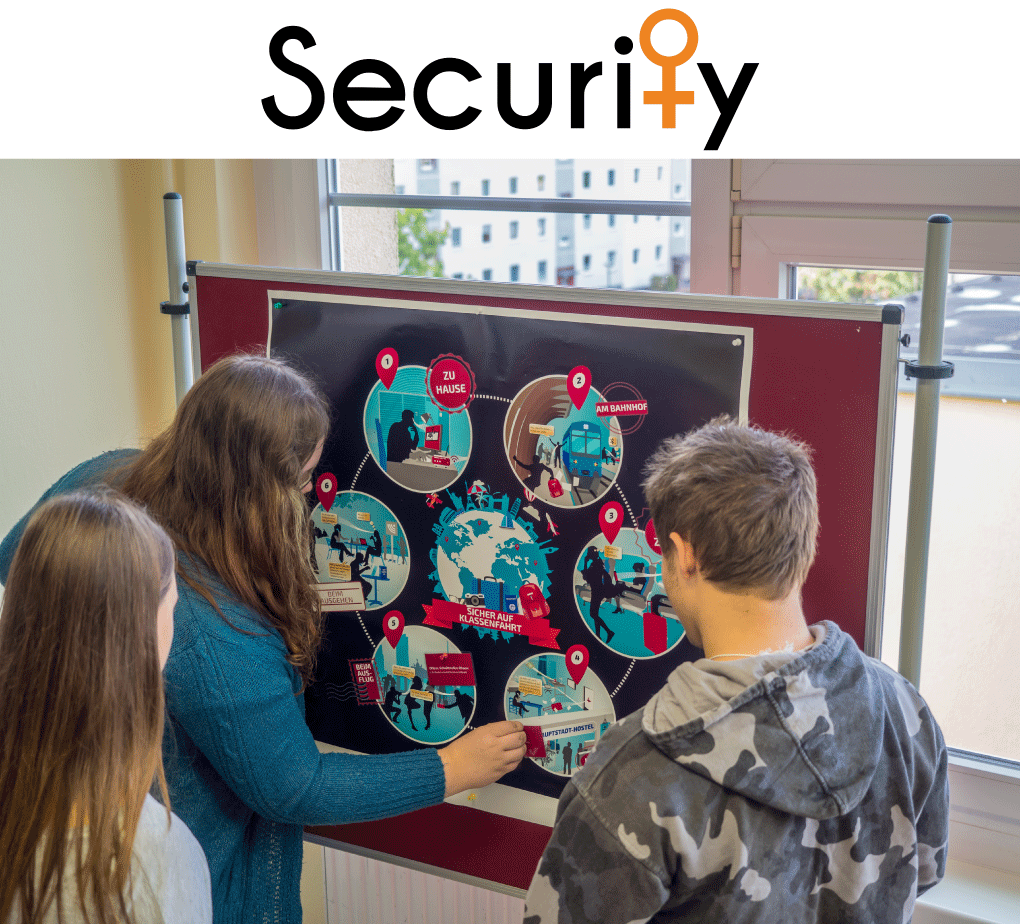
About the project
Objective
Two complex analogue game scenarios are to be developed and tested as part of the project Mittelstand 4.0-Kompetenzzentrum Stuttgart. These game scenarios will then be tested by the IT security working group. The aim is to sensitize the employees of small and medium-sized companies to the topic of information security in a playful way. To help implement these measures, the project’s cooperation partners and the working group itself are to be provided with the two game scenarios for their own events.
Fokus
The project is focused on devising and developing two complex analogue game-based learning scenarios for small and medium-sized companies with small digital additions. For the target group in the manufacturing sector, the learning scenarios are focused on social engineering, while the emphasis shifts to security risk management for the group comprising middle management in production.
Client
FZI Forschungszentrum Informatik
Methodology
Game-Based Learning
Analogue & Digital
Spiral of Transformative Interaction
Awareness
Learning scenarios
Social Engineering
The Federal Office for Information Security (BSI) understands social engineering as a method that exploits human characteristics such as helpfulness, trust, fear, and respect for authority to gain unauthorized access to information or IT systems [7]. According to the study “Bluff me if U can”, the term social engineering often has positive associations [8]. However, this type of interpersonal manipulation is one of the most frequent types of attack directed at companies in Germany for the purposes of data theft, industrial espionage, and sabotage [9].
Depending on the type of attack, a distinction can be made between technology-based and human-based social engineering attacks [10]. Technology-based attacks include phishing and the use of malware, while human-based attacks include identity change, identity theft, and shoulder surfing.
The game-based learning scenario to be developed will take up the various aspects and facets of social engineering, taking into account psychological principles, and will incorporate the needs and specific characteristics of the manufacturing industry.
Security Risk Management
In general terms, risk management is defined in ISO Guide 73 as “coordinated activities for the management and control of an organization, taking into account risks” [11]. Security risk management takes information security risks into account.
An introduction to risk management is provided by BSI Standard 200-3, which, among other things, provides guidance on threat identification, risk classification, and risk management so that the results can be integrated into the existing security concept [12]. The management of information security risks is also covered in ISO/IEC 27005 [13].
The learning scenario is intended to sensitize the management of SMEs to the fundamental importance of risk management and alert them to potential risks. The overall aim is to enable them to apply risk management, to detect weaknesses and thus to avoid and reduce risks, and, if necessary, to accept the residual risk. Risk management also includes communication with the security areas and the risk manager. The implicit intention of the scenario is therefore also to act as a kind of communication accelerator in mediating between management and security protagonists or risk managers.
Public Relations
- Project Results
- Scientific Publications
- Press

Project documentation

Moderation guide

IMCIC 2021 Florida
Social Engineering and Security Risk Management for SMEs in the Manufacturing Industry; Download as PDF or Videopresentation

WMSCI 2021 Florida

Märkische Allgemeine

Märkische Allgemeine
Other Projects
Team

Prof. Margit Scholl
Project Management
Stefanie Gube
Operational Project Management
Christin Walch
Project Team Member
Peter Koppatz
Project Team Member
Denis Edich
Project Team Member
Dietmar Pokoyski
Project partner known_senseContact
Bibliography
[1]
Buffum, P. S., Boyer, K. E., Wiebe, E. N., Mott, B. W.,
& Lester, J. C. (2015).
Mind the Gap: Improving Gender
Equity in Game-Based Learning Environments with Learning
Companions. In C. Conati, N. Heffernan, A. Mitrovic, &
M. F. Verdejo (Hrsg.), Artificial Intelligence in
Education: 17th International Conference, AIED 2015,
Madrid, Spain, June 22-26, 2015 (S. 64–73). Schweiz:
Springer International
Publishing. doi:10.1007/978-3-319-19773-9_7
[2]
Lombardi, M. (Januar 2007).
Authentic Learning for the
21st Century: An Overview. (D. G. Oblinger, Hrsg.)
Abgerufen am 30. April 2020 von
https://www.researchgate.net/publication/220040581_Authentic_Learning_for_the_21st_Century_An_Overview
[3]
Scholl, M., Fuhrmann, F., Edich, D., Ehrlich, P., Leiner, B., Scholl,
R., & Koppatz, P. (2017).
Das Projekt SecAware4job: Auf spielerischem
Weg zu erhöhtem Informationssicherheitsbewusstsein für den
Berufseinstieg. In TH Wildau (Hrsg.), Wissenschaftliche Beiträge 2017,
(S. 23-30). Wildau. doi:https://doi.org/10.15771/0949-8214_2017_3
[4]
Great Schools Partnership (Hrsg.). (19. September 2013).
Authentic Learning. Abgerufen am 30. April 2020 von
https://www.edglossary.org/authentic-learning/
[5]
Fuhrmann, F., Scholl, M., Edich, D., Koppatz, P., Scholl, L. R., Leiner, K. B., & Ehrlich, E. P.
(2017).
Informationssicherheitsbewusstsein für den Berufseinstieg (SecAware4job). Aachen: Shaker Verlag.
[6]
de Zafra, D., Pitcher, S., Tressler, J., & Ippolito,
J. (1998).
Information Technology Security
Training Requirements: A Role and Performance-Based
Model.
(National Institut of Standards and
Technology, Hrsg.) Gaithersburg.
Abgerufen am
03. Juni 2020 von
https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-16.pdf
[7]
BSI (Hrsg.). (2020).
IT-Grundschutz-Kompendium. Köln, Bonn: Reguvis Bundesanzeiger Verlag,
Bundesanzeiger Verlag. Abgerufen am 30. April 2020 von
IT-Grundschutz-Kompendium, S. 42
[8]
known_sense. (2015).
Studie: Bluff me if U can - Gefährliche Freundschaften am
Arbeitsplatz, Tiefenpsychologische Wirkungsanalyse Social Engineering
und seine Abwehr. (known_sense, Hrsg.) Köln.
Von
http://www.known-sense.de/BluffMeIfUCanAuszug.pdf
abgerufen, S. 36
[9]
Berg, A., & Niemeier, M. (6. November 2019).
Wirtschaftsschutz in der digitalen Welt. (bitkom, Hrsg.) Abgerufen am 30. April 2020 von
https://www.bitkom.org/sites/default/files/2019-11/bitkom_wirtschaftsschutz_2019_0.pdf,
S. 3
[10]
Albladi, S. M., & Weir, G. R. (2018).
User characteristics that influence judgment of social engineering
attacks in social networkes. (University Strathclyde: Human Centric
Computing and Information Science, Hrsg.) Glasgow:
SpringerOpen. doi:https://doi.org/10.1186/s13673-018-0128-7, S. 3
[11]
Klipper, S. (2015).
Information Security Risk Management: Risikomanagement
mit ISO/IEC 27001, 27005 und 31010
(2. Ausg.). Wiesbaden: Springer
Fachmedien. doi:10.1007/978-3-658-08774-6, S.44
[12]
BSI (Hrsg.). (2017).
BSI-Standard 200-3: Risikoanalyse auf der Basis IT-Grundschutz. Bonn.
Abgerufen am 05. Mai 2020 von
https://www.bsi.bund.de/SharedDocs/Downloads/DE/BSI/Grundschutz/Kompendium/standard_200_3.pdf
[13]
Bitkom (Hrsg.). (n.a.).
ISO/IEC 27005. Abgerufen am 05. Mai 2020 von
https://www.kompass-sicherheitsstandards.de/
https://www.kompass-sicherheitsstandards.de/Risikomanagement/ISO-IEC-27005